IoT is transforming businesses across industries. The technology has enabled businesses to optimize processes for efficiency and enhanced product offerings and helped them transform customer experiences. While industry leaders eagerly leverage business opportunities available through technology, IoT security is always a big concern.
This is due to two main reasons – incompatible solutions and immature security offerings that fail to secure deployments, putting the business at risk of cyberattacks like data breaches.
One sector that has witnessed a rapid increase in IoT adoption is healthcare. For instance, Chicago is installing cameras and sensors at most intersections. Their goal is to detect pollen count and air quality for its citizens. Or, the City of Newport deployed smart city IoT solutions to improve air quality, flood control and waste management. It’s easy to say IoT is the latest buzzword for discussion and implementation. n fact, according to Machina Research, the global IoT market is all set to reach $4.3 trillion by 2024.
However, while enterprises and states are eager to leverage IoT to bring better business opportunities, adopting a secure IoT security is still a concern to be thought about. In this article, we will discuss the common IoT security concerns across industries, the best practices to address those IoT security problems, and how you start your AWS journey to mitigate security and privacy in IoT.
IoT security vulnerabilities and challenges
One of the biggest reasons IoT ecosystems are not considered secure is that the connected features and devices are not ‘protected’ by default. There is also no automatic update to critical IoT security practices such as encrypted communication. So most of the connected devices in the ecosystem remain outdated, increasing IoT issues.
What makes IoT security concerns worse is that very few providers support the ability to patch the devices and gateways remotely after implementation. This further leaves room for security risks, as any connected devices can be hijacked.
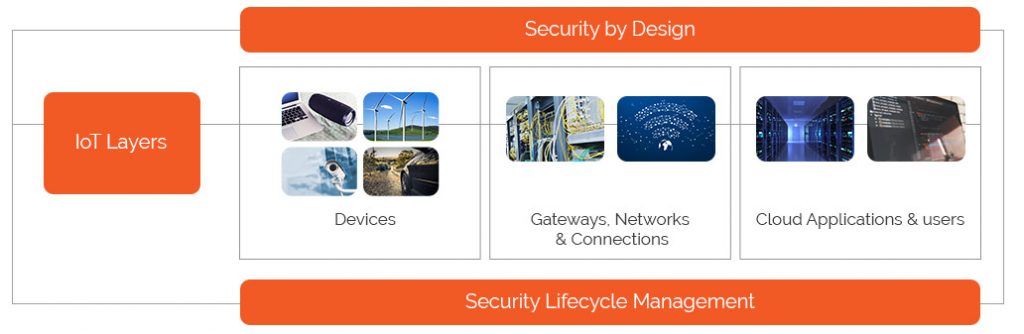
The main target points in the IoT layers are the devices, the network and connections, and the cloud infrastructure. With over 12,000+ malware strains being introduced into the digital landscape, there are many ways in which connected devices can be hacked into. The changing nature of these cyberattacks worsens IoT security problems.
“With 25 billion connected things by 2021, wireless networks and data will open new business opportunities. But it will also open doors to never-seen-before security threats.” Gartner
IoT security challenges are in every industry. Right from smart homes to manufacturing plants and connected cars, it is only the severity of the impact that varies—for example, a connected device in the healthcare IoT ecosystem. If the connected health device gets hacked, it might result in administering too much medication to a patient. This can be life-threatening.
Similarly, imagine IoT security problems in a water supply grid. An overflow without preparations can be disastrous. So how do you leverage IoT as technology and yet ensure security?
IoT security best practices
The measures you implement to address IoT security challenges vary depending on your application and your location in the ecosystem. But a few best practices that need to be followed across all industries and applications, including:
1. Incorporate security measures at the design phase
Devices in an IoT ecosystem share large amounts of sensitive data. Users connected to the network are also given the ability to control these devices. That makes it necessary to address security at the design phase of the ecosystem, and it needs to be dynamic. Applications must continually model, monitor and iterate the IoT security best practices.
Not most physical devices have a limited lifecycle. The constrained hardware for sensors, microcontrollers, actuators, and embedded libraries limit each device’s security capabilities. Therefore, please consider that the solutions you implement continuously adapt their architecture, firmware, and software to ensure IoT security.
2. Build on robust IT security and cybersecurity frameworks
When considering connecting thousands of devices and establishing connection points to create an IoT ecosystem, it is essential to ensure objects’ ability to exchange and use data. That’s where building this ecosystem on top of robust frameworks like AWS comes in to counter the Internet of Things security issues.
The AWS IoT core supports all industry-standard and customer protocols, adhering to best practices to address the Internet of Things security and privacy issues. This also allows devices in the ecosystem to communicate with one another even if they’re using different protocols.
Some of the benefits of using AWS to address IoT security challenges include:
- Easy scalability with the ability to repeat and reuse frameworks
- Promotes the compatibility of technology in the ecosystem
- Ensures interoperability across geographical boundaries
- Accelerates IT transformation
3. Measure impact to prioritize security measures
Cyber attacks are never identical. They also might not have the same impact on two businesses in the same industry. That’s why it is important to continually analyze the changing customer IoT ecosystems and how the devices operate within this ecosystem. This helps you identify the weakest points in the network that are prone to more significant risks.
Doing so is possible when you closely assess the risk impact and consequences. The analysis helps you derive actionable in terms of where your security efforts need to be directed.
4. PKI and other digital certificates
Another best practice for addressing the security vulnerabilities and challenges of the Internet of Things is establishing a public critical infrastructure (PKI). Along with 509 digital certificates, it plays a critical role in developing a secure IoT ecosystem. It provides the trust and control needed to identify public encryption keys, secure data exchanges over networks and verify object identities.
5. Consumer education and team integration
Consumers must be made aware of the Internet of Things security issues. They should then be equipped with the steps to ensure IoT security at all times – even as simple as updating their default credentials and applying software updates regularly.
Besides training your team on IoT challenges and issues, it is also essential to integrate siloed teams. For instance, you ask your technology developers to work closely with security specialists. This joint effort can ensure that proper controls are being added to objects in the ecosystem during the development phase, ensuring security and privacy in IoT.
Addressing IoT security issues with AWS
Embracing IoT in your business process requires you to rethink how industrial systems are designed and used. It requires you to identify processes that can be optimized using the technology and build security into the roots of the connected devices to shield them from cyber-attacks throughout their lifecycle.
Analyzing your business needs, vetting the available IoT security solutions and implementing them can be overwhelming. The chances of missing out on critical information might put you at a high-risk post-implementation.
That’s where AWS comes in. The cloud computing solutions implemented enable IoT to scale globally, lowering communication latency and allowing better responsiveness from the on-field devices.
AWS also offers a suite of IoT services. With services to operate and secure endpoints, gateways, platforms and applications in the ecosystem, as well as the traffic through the IoT layers, it simplifies the management and use of devices. This enables devices to interact with one another and transfer data continually, allowing companies to benefit from the technology without being prone to IoT risks and challenges( Learn more about it here ).
Simply put, AWS makes your IoT ecosystem more efficient while ensuring security at all endpoints.
But understanding the nuances of AWS and implementing the right solutions for your IoT application can be overwhelming. Working with AWS advanced consulting partners like Rapyder can help you tread the AWS journey easily.
Rapyder offers leading IoT security solutions and services to help you build a robust ecosystem. An ecosystem that protects all your connected objects through their entire lifecycle against the ever-changing nature of cyberattacks.
The IoT security team guides you every step of the way to ensure you get the most out of the technology. They assess your business’s current needs, evaluate your future needs and get you the right combination of reliable and scalable IoT security solutions that can adapt to changes without slowing down existing processes.
So whether you’re re-evaluating an existing connected device or designing a new one, it’s time to get Rapyder on your side.
To get the latest insights, research and expert articles on AWS Services, Cloud Migration, DevOps and other technologies, subscribe to our Blog Newsletter here. For AWS Case studies and success stories, visit Case Study Section




